Working with Multiple Service Principal Names
The can be configured to handle multiple Service Principal Names (SPN) in a Kerberos keytab file. This allows the Gateway to perform Kerberos authentication in these scenarios:
gateway83
The
API Gateway
can be configured to handle multiple Service Principal Names (SPN) in a Kerberos keytab file. This allows the Gateway to perform Kerberos authentication in these scenarios:- Scenario 1:One Gateway cluster that has been assigned multiple DNS host names, each with their own Virtual IP (VIP):Multiple_Service_Principal_Names2
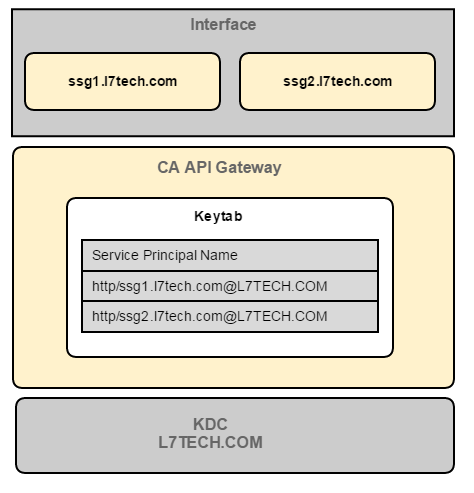
- Scenario 2:Multiple domains:Multiple_Domains_Name_Services
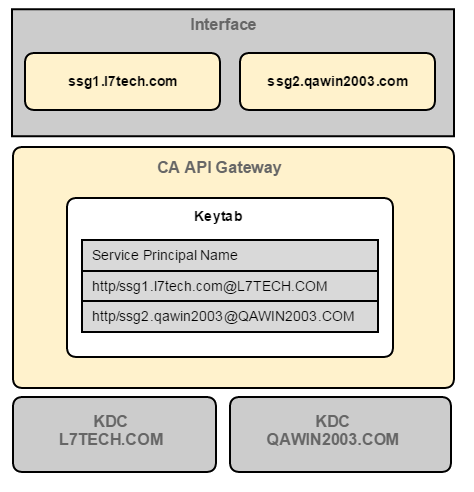
- Scenario 3:Routing to multiple domains (using the Route via HTTP(S) Assertion).
To enable the Gateway for multiple Service Principal Names:
- Open thesystem.propertiesfile in a text editor./opt/SecureSpan/Gateway/node/default/etc/conf/system.properties
- Add the following property:com.l7tech.kerberos.useSpnFromInboundTicket=true
- Save and close the file.
To create multiple service principals in the keytab file (Windows)
:- On the Active Directory machine, run the following command:ktpass - princ http/<Gateway_host>@<Realm>- mapuser<userName>-pass<userPassword>-in<kerberos_file_to_merge>- out<keytab_name>For example:ktpass -princ http/gateway.domain.com@DOMAIN.COM -mapuser gateway -pass password - in kerberos.keytab -out kerberosMerged.keytabThis produces the output filekerberosMerged.keytabwhich contains the multiple service principals. Install this keytab using Manage Kerberos Configuration.
To create multiple service principals in the keytab file (Linux)
:- Copy the keytab to your Samba or UNIX server.
- Run thektutilcommand on your Samba or UNIX server to merge your existing and new keytab together:ktutil:ktutil: read_kt keytab-number1ktutil: read_kt keytab-number2ktutil: write_kt krb5.keytabktutil: quitOnce this is done, install the keytab file using Manage Kerberos Configuration.
How the Gateway Determines the Principal
When multiple service principals are defined, this is how the various assertions determine which principal in the keytab to use:
- Require Windows Integrated Authentication Credentials AssertionFor this assertion, the Gateway uses the request URI to determine which principal in the keytab is used to handle the Windows authentication.Example: For a request for the http://ssg1.acmecorp.com/test.html page, the Gateway look up the service principal "http/ssg1.acmecorp.com" from the keytab file.
- Route via HTTP(S) AssertionFor this assertion, the Gateway use the routing URI to determine which principal in the keytab is used to handle the Windows authentication.Example:Routing to thehttp://ssg1.acmecorp.com/test.htmlpage, the Gateway looks up the service principal "http/ssg1.acmecorp.com" from the keytab file.
- Require WS-Security Kerberos Token Profile Credentials AssertionThis assertion requires the use of theAPI Gateway-XML VPN Client.The Gateway uses the host name entered in the Gateway Account Properties (in the XML VPN Client) to determine which principal in the keytab is used to handle the Windows authentication.The Kerberos Name is not required unless the Kerberos name does not match the standard naming pattern "http/<GatewayHostName>".