Differences Between the Container Gateway and Appliance Gateway
The Container Gateway is similar to the traditional Appliance Gateway, with the following notable differences:
gateway93
The Container Gateway is similar to the traditional Appliance Gateway, with the following notable differences:
Operational Differences
Container Gateway | Appliance Gateway | |
Compatibility |
For more information on compatibility, see Container Gateway Platform Support. |
|
Distribution |
|
|
Deployment |
|
|
Configuration |
|
|
Management |
|
|
Updates |
|
|
Health Check |
|
|
Logging |
|
|
Monitoring |
|
|
Diagnostics |
|
|
Security |
|
|
CA Single Sign-On |
|
|
Firewall rules |
|
|
Networking |
|
|
|
| |
Hardware Security Module (HSM) |
| Supports these HSMs: |
Cluster management |
|
|
Backup/Restore |
| |
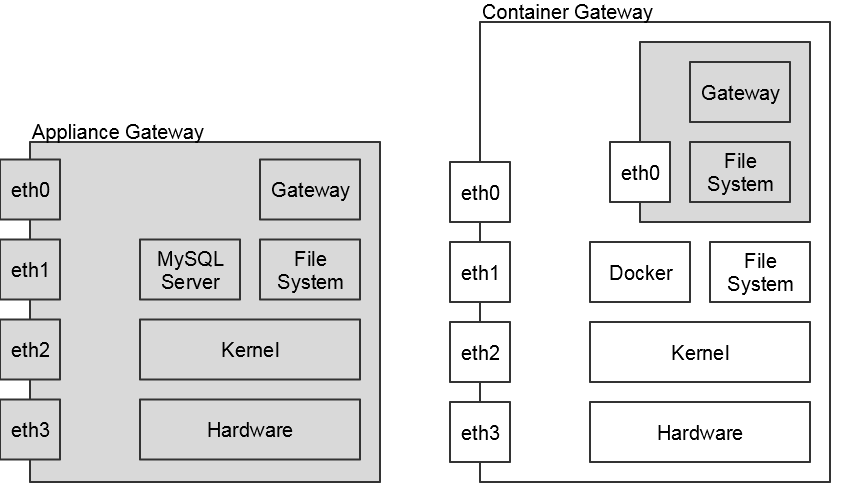
Architecture Differences
While the Container Gateway operates largely similar to the Appliance Gateway, differences exists at the architecture level due to the different deployment architectures.
- When running a container, each container gets its own private file system that differs from the one on the host.
- Each container gets exactly one network interface that uses Network Address Translation (NAT) through the physical interfaces.
- There is no MySQL server running in the Container Gateway. Instead, you need to run their own server (such as handling replication setup, backup/restore, and monitoring).
- The Container Gateway cannot access the hardware layer of the machine. This prevents the use of Hardware Security Modules (HSM).
The differences in architecture result in a change in what you build and/or configure. In the diagram below, the changed areas are highlighted in gray.
Architecture_differences