Working with CA Single Sign-On
The Policy Manager provides functionality to authenticate and authorize against a CA Single Sign-On Policy Server. This topic describes how to use this functionality to perform common tasks with CA Single Sign-On.
gateway91
The Policy Manager provides functionality to authenticate and authorize against a CA Single Sign-On Policy Server. This topic describes how to use this functionality to perform common tasks with CA Single Sign-On.
(1) The CA Single Sign-On feature requires the CA Single Sign-On Agent SDK v12.52, which comes pre-installed in the hardware and virtual appliance versions of the
CA API Gateway
. If you are running the software Gateway, refer to Install the CA Single Sign-On SDK for Software Gateways for instructions. (2) CA Single Sign-On is not compatible with the CA API Developer Portal - SaaS product.Configure System Property for CA Single Sign-On
Before you start using CA Single Sign-On, configure the following system property first.
To configure the system property for CA Single Sign-On:
- Open a privileged shell.
- Locate and open the following file in a text editor:/opt/SecureSpan/Gateway/node/default/etc/conf/system.properties
- Add the following line:org.apache.tomcat.util.http.ServerCookie.ALLOW_EQUALS_IN_VALUE = true
- Save and exit the file.
- Restart the Gateway.
Create a CA Single Sign-On Configuration
You should create a CA Single Sign-On configuration first before performing any other CA Single Sign-On-related tasks.
To create a CA Single Sign-On configuration
:- Run the Manage CA Single Sign-On Configurations task.
- Click [Add] to open the CA Single Sign-On Configuration Properties.
- Click [Register] and complete the CA Single Sign-On Registration Properties.
- When the registration properties are entered, complete the CA Single Sign-On Configuration Properties by entering a Configuration Name.
- Click [Test] to check whether your configuration is valid.
For more information, see Manage CA Single Sign-On Configurations.
Basic User Authentication Using CA Single Sign-On Assertions
The steps below provide an overview on how to use the CA Single Sign-On assertions to perform basic user authentications.
- Ensure that an end point has been created on theAPI Gateway.
- Add the Check Protected Resource Against CA Single Sign-On Assertion to your policy.Configure the assertion to use a valid CA Single Sign-On configuration, agent name, protected resource, and action. Keep the default variable prefix.
- Add the Require HTTP Basic Credential Assertion to the policy.
- Add the Authenticate Against CA Single Sign-On Assertion to the policy. Use the default settings.
- Add the Authorize via CA Single Sign-On Assertion to the policy, ensuring that it comes after the Authenticate Against CA Single Sign-On Assertion.
- Complete your policy by adding other assertions as required.

Basic User Authentication via HTTP Cookie using CA Single Sign-On Assertions
The steps below provide an overview on how to use the CA Single Sign-On assertions to perform basic user authentication using an HTTP cookie.
- Ensure that an end point has been created on the Gateway.
- Add the Check Protected Resource Against CA Single Sign-On Assertion to your policy.
- Configure the assertion to use a valid CA Single Sign-On configuration, agent name, protected resource, and action. Keep the default CA Single Sign-On variable prefix.
- Add the At Least One Assertion Must Evaluate to True Assertion to the policy. This folder serves as the parent to the two folders in steps 4 and 5.
- Add the All Assertions Must Evaluate to True Assertion as the first child to the above "At least..." folder. Into the "All assertions..." folder, add the following assertions:
- Add the Require HTTP Cookie Assertion and configure it as follows:
- Cookie name:SMSESSION
- Variable prefix:cookie(default)
- Add the Authenticate Against CA Single Sign-On Assertion and configure it as follows:
- Select theUse SSO Token from Context Variablecheck box
- Enter the name of the cookie variable from the Require HTTP Cookie Assertion (for example, "cookie.SMSESSION").
- Add the Authorize via CA Single Sign-On Assertion to the policy, ensuring that it comes after the Authenticate Against CA Single Sign-On Assertion. Configure it as follows:
- Select theUse SSO Token from Context Variableradio button
- Enter the name of the cookie variable from the Require HTTP Cookie Assertion (for example, "cookie.SMSESSION").)
- Add another All Assertions Must Evaluate to True Assertion as the second child to the above "At least..." folder (step 3). Into this "All assertions..." folder, add the following assertions:
- Add the Authenticate Against CA Single Sign-On Assertion and configure it as follows:Select theUse SSO Token from Context Variablecheck box.Enter the name of the cookie variable from the Require HTTP Cookie Assertion (for example, "cookie.SMSESSION").
- Add the Authorize via CA Single Sign-On Assertion to the policy, ensuring that it comes after the Authenticate Against CA Single Sign-On Assertion. Configure it as follows:Select theUse SSO Token from CA Single Sign-On Contextradio button.
- Complete your policy by adding other assertions as required.
_.png)
Advanced CA Single Sign-On with Status Check of Session
The CA Single Sign-On assertions can be used in advanced CA Single Sign-On authentication/authorization scenarios, such as collecting user credentials based on the information returned from the assertions, and responding to error conditions.
The following policy is an example of advanced CA Single Sign-On authorization with status checking of the session.
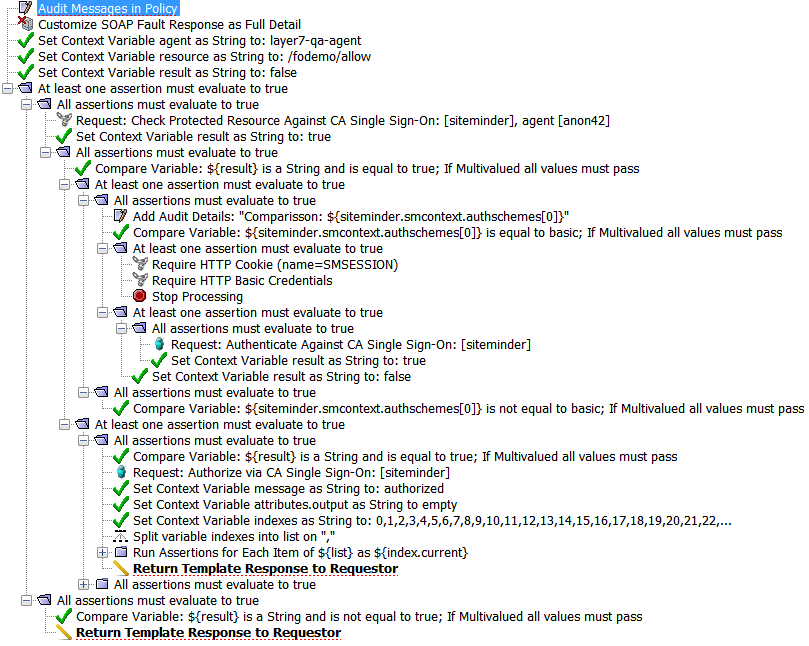
Troubleshooting CA Single Sign-On
See CA Single Sign-On Errors for more information.