Working with JSON Web Tokens
This topic describes how to use JSON Web Tokens (JWT) in the gateway. The sample workflow shows you how to use all the related assertions: , , and .
gateway83
This topic describes how to use JSON Web Tokens (JWT) in the
CA API Gateway
. The sample workflow shows you how to use all the related assertions: Encode JSON Web Token Assertion, Decode JSON Web Token Assertion, and Create JSON Web Key Assertion. Contents:
Terminology
Term | Meaning |
JWT | JSON Web Token |
JWK | JSON Web Key |
JWKS | JSON Web Key Set |
alg | Signature algorithm |
iss | JSON Web Token issuer |
exp | Expiry date (of the JSON Web Token) |
kid | JSON Web Key ID |
Scenario
You are validating a JSON Web Token signature using a JWK. You are validating against an expected signature algorithm, JWT issuer, and JWT expiry date.
Sample Policy
The following sample policy achieves the Scenario described above.
For simplicity, the sample policy uses hard-coded values where context variables must be used in a real policy. Proper error handling is omitted in this sample. Ensure that this policy is part of the service that it is authenticating.
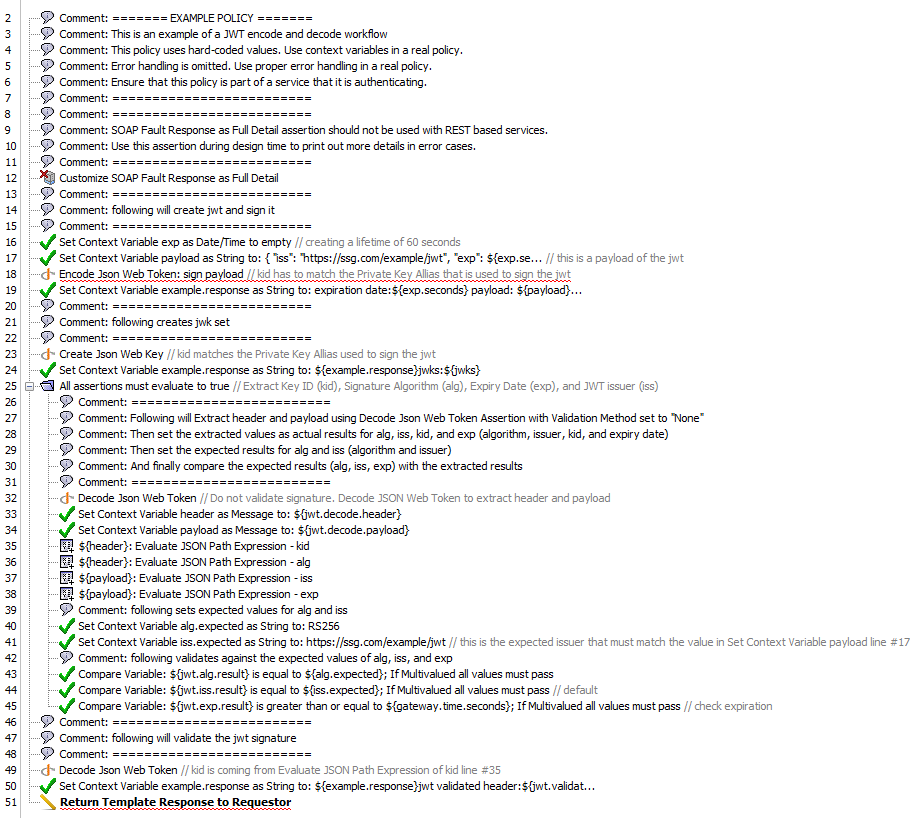
Concise summary of the process:
- Create a JWT and sign it using the Encode JSON Web Token Assertion.
- Create a JWKS using the Create JSON Web Key Assertion.
- Extract the header and payload using the Decode Json Web Token Assertion (withValidation Methodset to "None").
- From the extracted header and payload, set extracted results foralg,iss,kid, andissusing Evaluate JSON Path Expression Assertion.
- Set the expected results foralgandiss.
- Compare the expected results against the extracted results (alg,iss,exp).
- Finally, validate the JWT signature using Decode JSON Web Token Assertion.
Try it Yourself
Download the encode_decode_jwt_example_policy.xml attached to this topic and then import it into your Policy Manager.
Try validating against a different, unexpected algorithm, to see the policy fail as expected. Do this by changing line 40: "Set Context Variable alg.expected as String to: RS256". Change the expression from "RS256" to "HS256".