Verifying Hostnames for Outbound SSL Connections
Part of the SSL Trust behavior in the is to ensure that the hostname in a server's SSL certificate matches the hostname used in the outbound SSL request. However, you can suppress this verification for testing purposes or for added flexibility in your production environment, if you are confident that allowing mismatched hostnames will not impair security.
gateway83
Part of the SSL Trust behavior in the
API Gateway
is to ensure that the hostname in a server's SSL certificate matches the hostname used in the outbound SSL request. However, you can suppress this verification for testing purposes or for added flexibility in your production environment, if you are confident that allowing mismatched hostnames will not impair security.The
API Gateway
uses a two layer system to determine when hostnames should be verified:- the setting Verify Hostnames for Outbound SSL Connections in the [Validation] tab of a certificate's properties
- the setting of theio.httpsHostVerifycluster propertyHostname verification proceeds only when PKIX validation of the TLS server certificate has succeeded. If the server certificate is not trusted, the connection fails and hostname verification is not performed.
The hostname verification procedure applies to any assertion that performs outbound TLS; examples of such assertions include:
- Exchange Credentials using WS-Trust
- Route via HTTP(S)
- Retrieve SAML Browser Artifact
- Use WS-Federation Credential (both Request and Exchange modes)
The following diagram describes how the
API Gateway
determines whether to use the certificate setting or the API Gateway
cluster property:Verify Hostnames
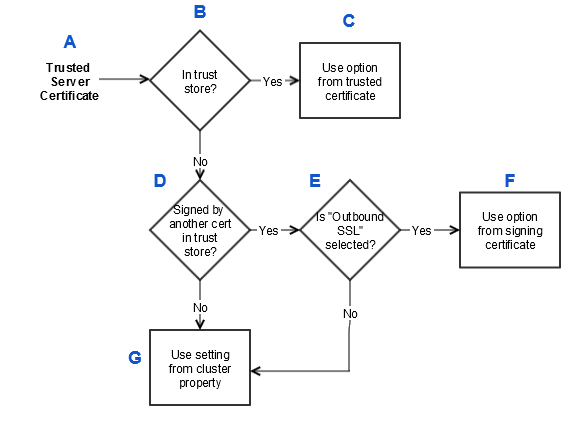
The following table describes each step in the process:
Flowchart step | Description |
|---|---|
A. Trusted Server Certificate | This is a certificate that is either issued by a trusted certificate authority, by another trusted certificate in the API Gateway , or has been added to the API Gateway trust store. Hostname verification can proceed only if the server certificate is trusted. |
B. In trust store? | Has the server certificate been added to the API Gateway trust store? |
C. Use option in certificate | If B is 'Yes', then use the hostname verification option from the trusted certiciate. The io.httpsHostVerify cluster property is not consulted in this case. |
D. Signed by another cert in trust store? | If B is 'No', then is the certificate signed directly by another certificate in the trust store? |
E. Is "Outbound SSL" selected? | If D is 'Yes', does the signing certificate have its "Signing Certificates for Outbound SSL Connections" option selected? This option appears in the Certificate Properties, under the [Options ] tab. |
F. Use option from signing certificate | If E is 'Yes', then use the option from the signing certificate. The io.httpsHostVerify cluster property is not consulted in this case. |
G. Use setting from cluster property | If D or E is 'No', then use the io.httpsHostVerify cluster property setting. |